Events like stock splits or changes in the list from the companies composing the index alter the sum from the part prices. In these cases, in order to stay away from discontinuity in the index, the Dow Divisor is updated so that the quotations right just before and following the party coincide:
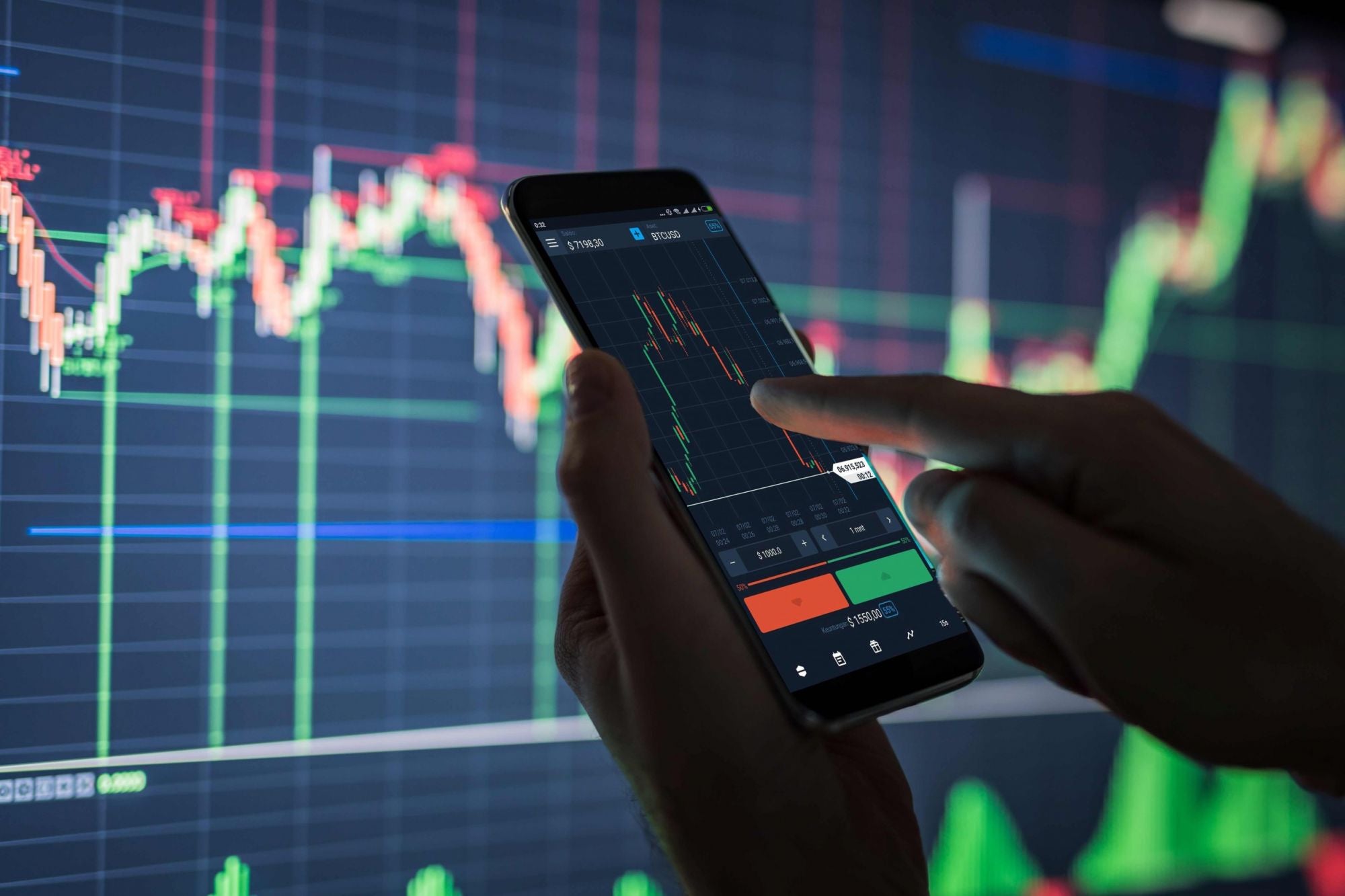
Sometimes your fees are very low but sometimes your fees are substantial - it really just will depend on the charge construction in the exchange plus the state of your orderbook in the intervening time.

Once the rate of requests has dropped down below the brink for 10 minutes, the user might resume accessing articles on SEC.gov. This SEC follow is meant to limit extreme automatic searches on SEC.gov and isn't supposed or expected to affect folks browsing the SEC.gov Web page. Take note that this plan may perhaps change as being the SEC manages SEC.gov to ensure that the web site performs efficiently and remains accessible to all users.
Though the Fund has a daily investment goal, chances are you'll hold Fund shares for longer than sooner or later if you suspect it really is reliable with your plans and threat tolerance.
Regardless of whether the impression is overblown because of the media, it’s a actuality that the fundamental expense of mining will be the Electrical power consumed. The income from mining needs to outweigh those fees, furthermore the original investment into mining components, in order to become profitable.
A virtual honeynet is 1 that, though showing up being a physical network, is often a virtual image of the network that resides on only one server. As it is not a network technique, computer security analysts do not need to squander their time examining legit users present in real-world networks.
Find More › Does Warren Buffett very own silver? He is an expert on individual finance, corporate finance and real estate and has assisted Many clients in meeting their financial objectives over his occupation.
Network honeypots surface susceptible and undefended but are isolated and monitored. This is why, website the suspect information is much far more apparent than It will be within an genuine network, where it would need to be tracked down amid each of the legit network targeted visitors and data. Apps within a honeynet typically have familiar names like finance
The first miner to discover the solution to the problem gets bitcoins for a reward, and the method begins yet again.
But it can help to acquire a historical viewpoint. Allow’s look at a lengthy-phrase chart of equally metals masking 1960-2024. Silver is blue and gold is yellow.

EH (Licensed Moral Hacker) certification presents pupils the right combination of theoretical awareness and useful abilities they need for the career in the field of ethical hacking.
How we use your information depends on the item and service that you utilize along with your marriage with us. We may possibly use it to:
In countries where mining is illegitimate or its Electricity use is taxed at a higher stage, an increase in Electricity use from mining might draw interest. It really is best to comply with your jurisdiction's legislation when contemplating Bitcoin mining.
By using This web site, you will be agreeing to security checking and auditing. For security purposes, and to ensure that the public service stays available to users, this government computer program employs programs to observe network traffic to recognize unauthorized makes an attempt to upload or change information or to usually induce destruction, like attempts to deny service to users.
Best address
https://www.forex.com